Challenge link: https://tryhackme.com/room/easyctf
Challenge Difficulty: Easy
Challenge Tags: security, enumeration, privesc
Reconnaissance & Scanning
From the THM platform, I got 10.10.56.199 as the target machine.
Question 1: How many services are running under port 1000?
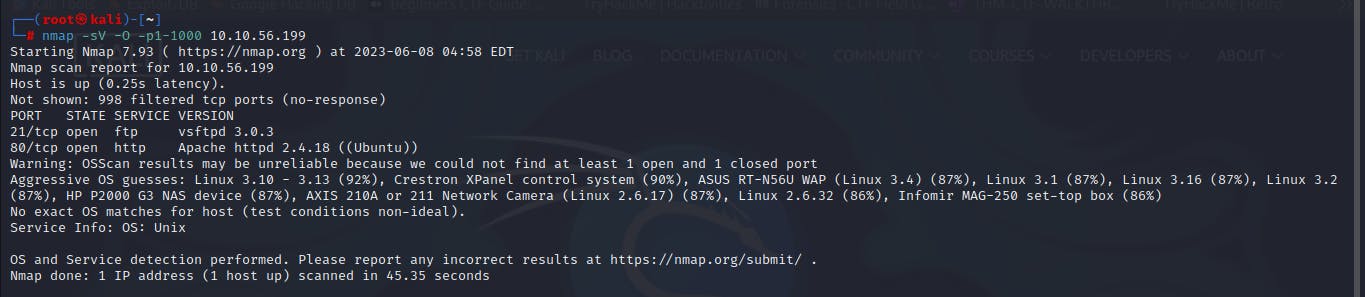
Using the command
nmap -sV -O -p1-1000 10.10.56.199I was able to identify two (2) ports between under 1000.The
-p1-1000switch specifies the range of ports to consider during a nmap scan. If not explicitly specified during the scan, nmap scan 1000 of the most common ports.
Question 2: What is running on the higher port?
- Using the command
nmap -sV -O 10.10.56.199I identified ssh as being the service running on the highest port.

Question 3: What's the CVE you're using against the application?
I began further enumeration starting with port 80 hosting the HTTP server.
Pasting the IP address onto a browser did not yield results, as I was directed to an Apache landing page.
I then decided to do subdomain enumeration to find hidden directories on the HTTP port using
gobuster dir -uhttp://10.10.56.199-w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt

- I found a directory
/simpleand instantly tried accessing it from the browser.

It was another landing page for a content management system (CMS) which I assumed was going to be our entry point or possible angle for an initial foothold.
After some scrutinization of the webpage, I found the CMS name and version at the bottom of the page, which I then did a Google search for to find the Common Vulnerabilities and Exposures (CVEs) it can succumb to.

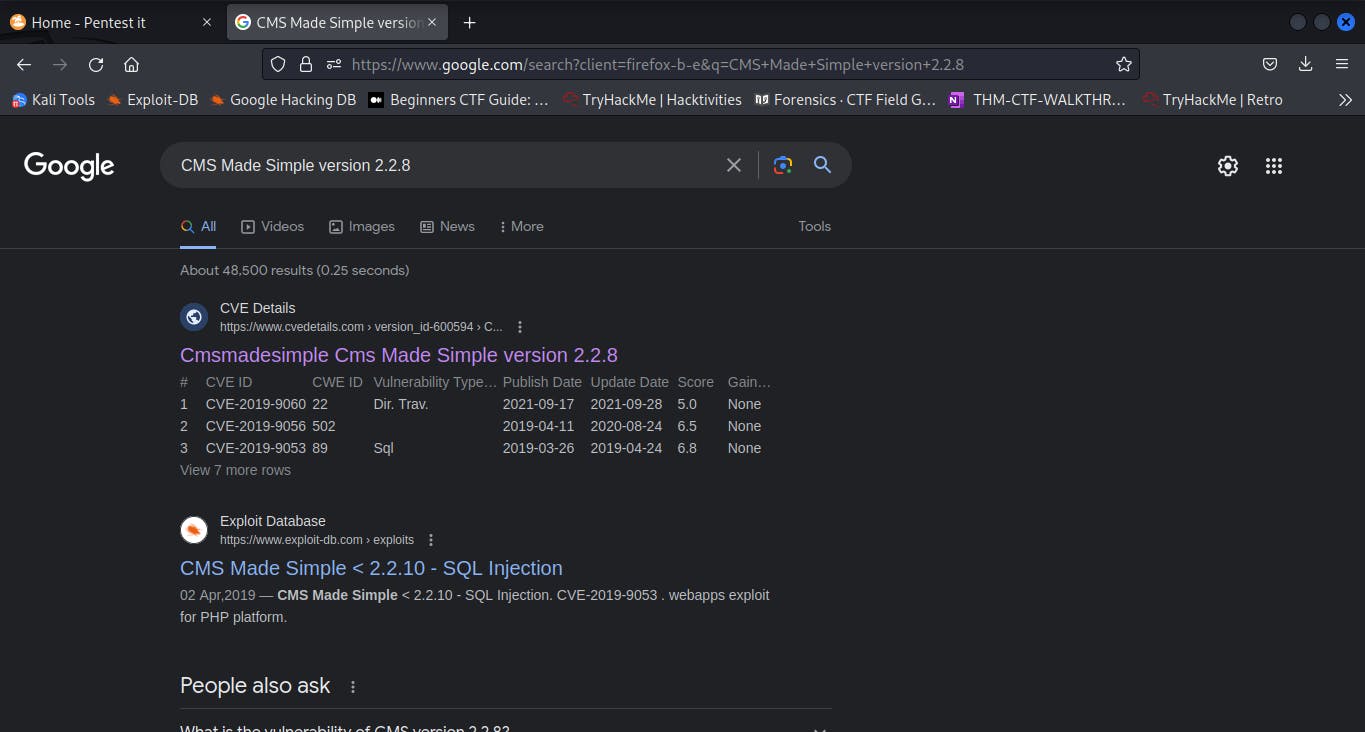
- After visiting the CVE details website and going through the possible exploits I managed to identify CVE-2019-9053 as being the correct exploit for this challenge.

Question 4: To what kind of vulnerability is the application vulnerable?
- From reading the CVE description I gathered that it was an SQL Injection vulnerability, also known as 'SQLi'.

Exploitation
Question 5: What's the password?
- I moved on to download the exploit script of the CVE from exploit-db.

- The script was saved as 46635.py so running
nano 46635.pydisplayed the contents of the script.

- The script was made in Python but because it was compiled in python2 I had to change the syntax to python3 because it was giving errors. I downloaded 2to3 to change file compatibility with the code below:
pip install 2to3
pip3 install 2to3
python -m pip install 2to3
python3 -m pip install 2to3
py -m pip install 2to3
- After running
2to3 -w 46635.pythe file was successfully converted and I could finally run the exploit.
- To run the exploit, I had to add the target URL and a wordlist path as the parameters of the command:
python346635.py-uhttp://10.10.56.199/simple/-w /usr/share/wordlists/rockyou.txt

From the results I got, I found the username
mitchand a password hash. I later discovered that I had to add another switch--crackwithin the command for the password hash to be cracked.I tried running the exploit again
python346635.py-uhttp://10.10.56.199/simple/--crack -w /usr/share/wordlists/rockyou.txtwith the switch but it showed null results.
NB: I assume that part of the code got broken when I converted it from python2 to python3, so I left this angle as a dead-end to try out a different attack vector.
- I returned to the FTP port
ftp 10.10.56.199and tried the popular 'anonymous' login - this gave me access to the FTP server!

I used
lsto view the contents of the server and found one folder labelled 'pub', I navigated to the folder withcd puband ranlsagain to view the contents of this folder, and I discovered a text file labelled 'ForMitch.txt'I downloaded the file onto my local machine using
mget ForMitch.txtand I viewed the file withcat ForMitch.txt.

From the message context, I figured that there was a user called
mitchconsidering that we found the same username from the exploit script earlier. And I also assumed that there was a way to brute force the password since that message also suggested that it cracked in a short time.Using
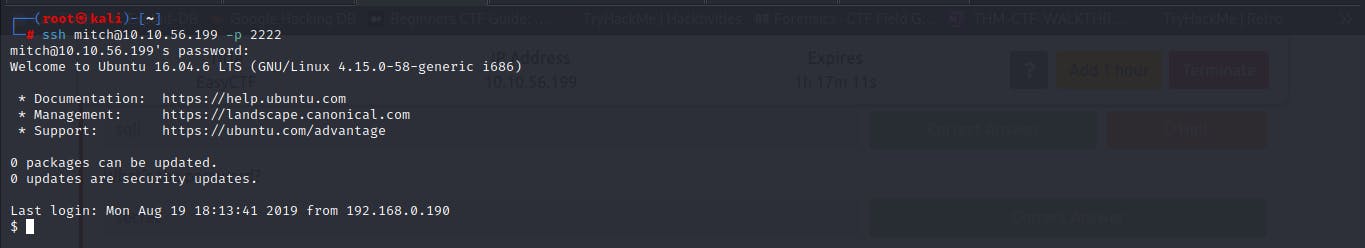
hydra -l mitch -P /usr/share/wordlists/rockyou.txt ssh://10.10.56.199:2222I tried brute forcing the SSH port usingmitchas the username.
NB: It was necessary to specify the port 2222 since the tools are accustomed to port 22 as the default SSH port.

- Results from Hydra gave us the password 's*****'.
Initial Foothold
Question 6: Where can you log in with the details obtained?
Attempting to gain access to the server via SSH with
mitchas the username ands*****as the password gave us an initial foothold.'SSH' was the answer to question 6.
Question 7: What's the user flag?
lsshowed that there was auser.txtfile in the home directory, runningcat user.txtdisplayed the first flag.

Question 8: Is there any other user in the home directory? What's its name?
- I ran
pwdto see the name of my current directory, then I rancd ..to navigate back to the home directory.lsgave me the name of the other folder present in the home directory'sunbath'which was the answer to this question.

Privilege Escalation
Question 9: What can you leverage to spawn a privileged shell?
For privilege escalation, I first used
sudo -lto find binaries I could run as the current user and foundusr/bin/vim.I went to GTFOBins and looked for a SUDO shell escape script for Vim.
The script I found was as follows:
sudo vim -c ':!/bin/sh'



- The answer to this question is 'vim'.
Question 10: What's the root flag?
I ran
cd ../..to navigate into the root directory.By navigating to the root folder using
cd rootandlsto view the contents of the directory I found the root.txt file,cat root.txtto reveal the final flag!


![Simple CTF [TRYHACKME - EASY]](https://cdn.hashnode.com/res/hashnode/image/upload/v1686214469228/fefaba84-fa5d-4fb0-89bc-6b58b910393f.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)