General Remarks
CTF Page Link: https://compete.metactf.com/
DawgCTF was accommodative of all levels of expertise (Beginner Friendly) - and the challenges gave a fair chance for all CTF players to learn and nurture their hacking skills.
Ram Analyzer
Challenge Context
Can you figure out how much RAM I've got installed in my computer? I can't figure out how to open the case.
Flag format should be DawgCTF{NUMBERGB}
Solution
- The challenge description came with an attached Desktop Management Interface (DMI) output as a text file.
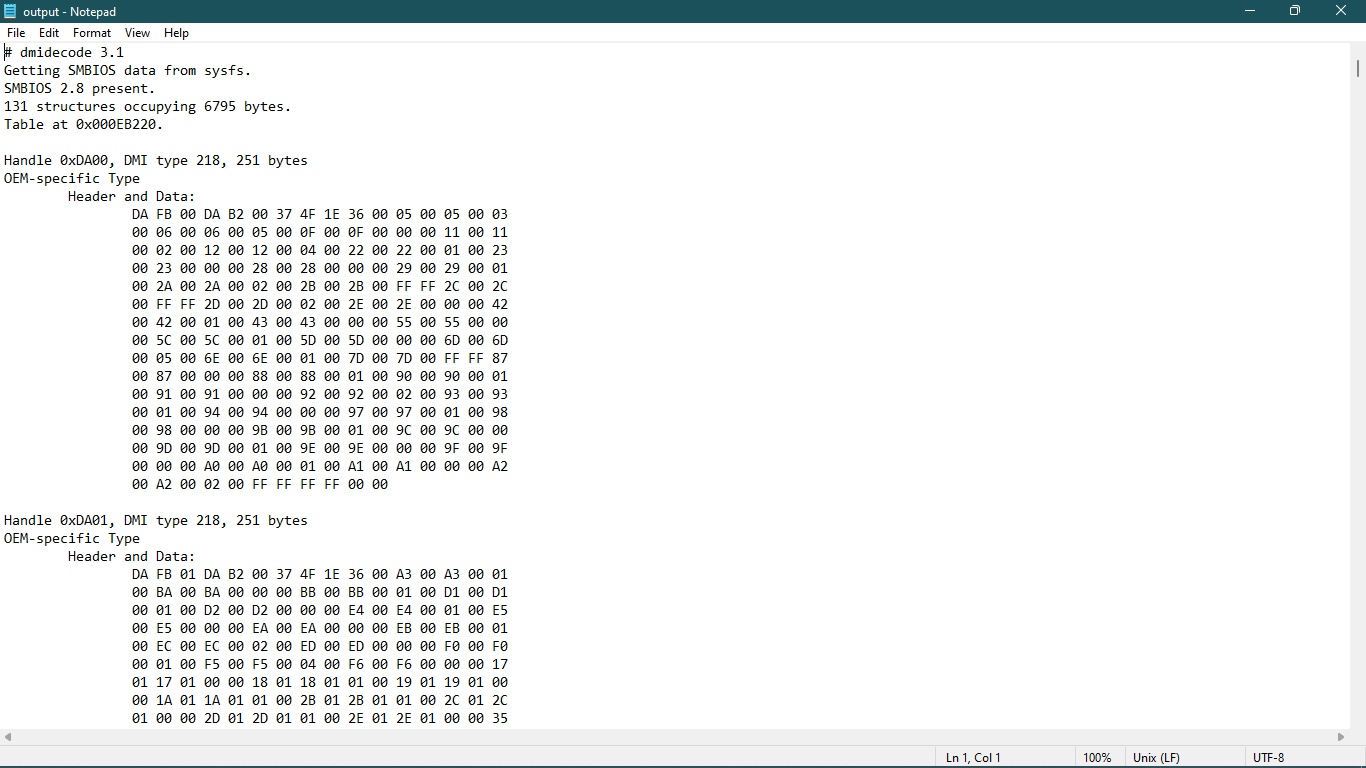
- To solve this challenge, we use a Python script to sum all the sizes in the DMI type 17 modules and the result is the total installed RAM on the machine.
import re
with open('output.txt', 'r') as file:
file_content = file.read()
memory_sizes_mb = re.findall(r'(\d+)\s*MB', file_content)
memory_sizes_mb = [int(size) for size in memory_sizes_mb]
total_memory_mb = sum(memory_sizes_mb)
print("Memory Sizes for RAM Modules:")
for i, size in enumerate(memory_sizes_mb, 1):
print("RAM Module {}: {} MB".format(i, size))
print("Total Memory Size: {} MB".format(total_memory_mb))
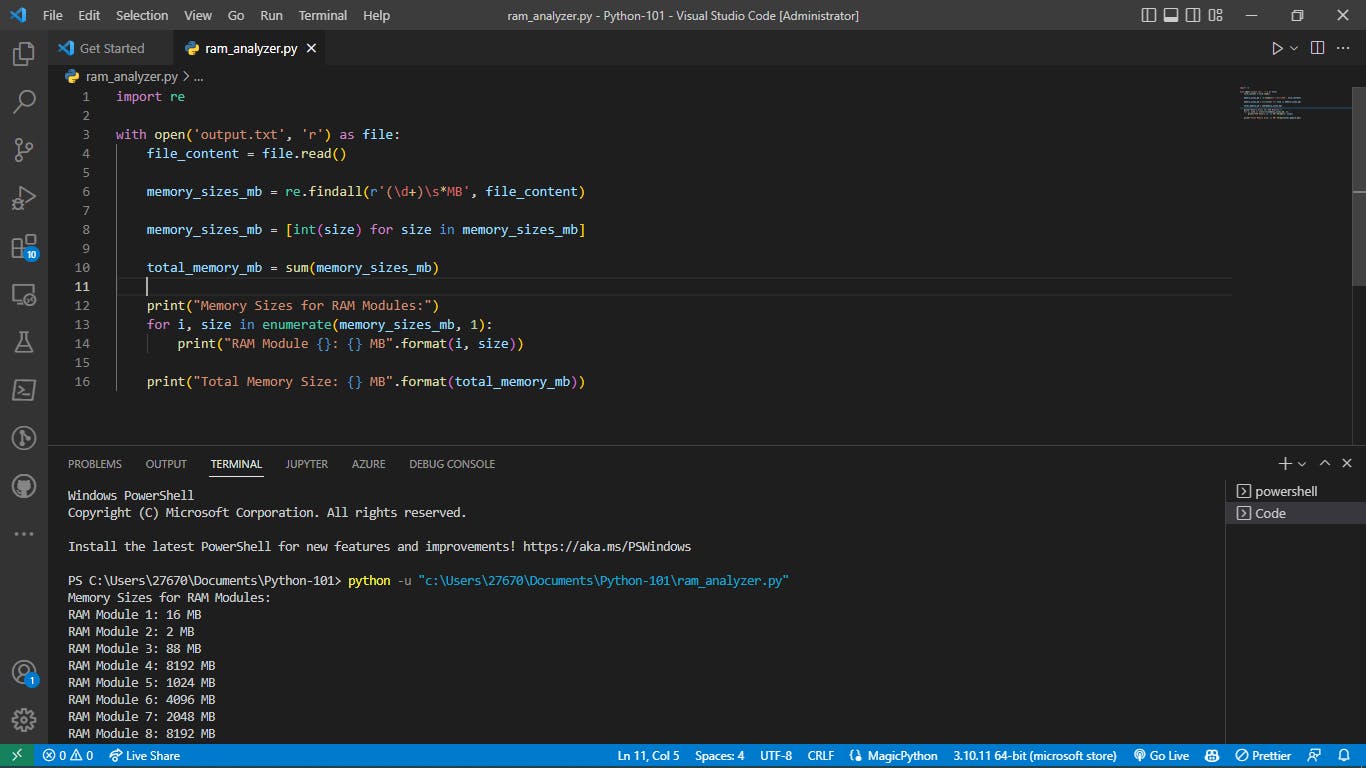
- The output is as follows:
Binary Bomb Phase 1
Challenge Context
Starting off with small strings...
Same Files For All Binary Bomb: View Files Here
You may enter SKIP to skip a phase or HELP to access the help menu.
Solution
The challenge description came with an attached binary file labelled
dawg_bbomb.I used
strings dawg_bombband I discovered the first flag in plain text.

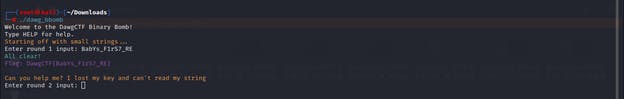
After using this flag as input for the first round of the challenge, I proceeded to the second phase.
Note that you might have to add execute permissions to the binary file with
chmod +xso that the binary runs.
Celestial Caper
Challenge Context
Isn't the lunar surface cool? Surely, though, there's more than what meets the eye! The solution will be case insensitive, and contain only characters a-z. The flag format will be DawgCTF{solutioninlowercase}

Solution
The challenge description came with the above image attached.
Using the Lunar Alphabet Translator from https://www.dcode.fr/lunar-alphabet-leandro-katz I was able to match the provided images to their respective moon phases and the flag was revealed.
Birds!
Challenge Context
A charm of sparrows land on the railing next to you, you think they are trying to tell you something.

Solution
The challenge description came with the above image attached.
Using the Bird on a Wire Cipher from https://www.dcode.fr/birds-on-a-wire-cipher I was to match the birds on the provided image to the ones on the deciphering scale and the flag was revealed.


String Things
Challenge Context
I got this binary file called "secrets", and I really wanna know whats in it. But it asks me for a password, and I have no idea what it is! Maybe you can figure it out?
Solution
The challenge description came with a binary file labelled ''secrets".
I changed the file permissions using the command
chmod 777 secretsso that the binary has execute permissions.Upon running the binary with the command
./secretsit prompted me to enter a password. I closed the program and used the commandstrings secretsto see the text (or printable character sequences) in a binary file.
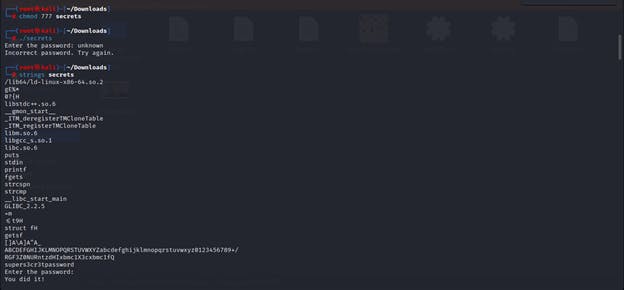
I noticed the text
supers3cr3tpasswordwhich I assumed was the required password to access the binary.After running the binary again using
./secretsand usingsupers3cr3tpasswordas the password I managed to retrieve the challenge flag.


